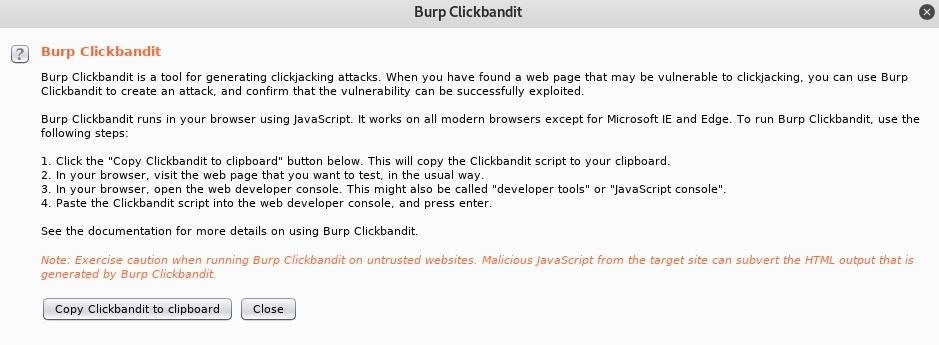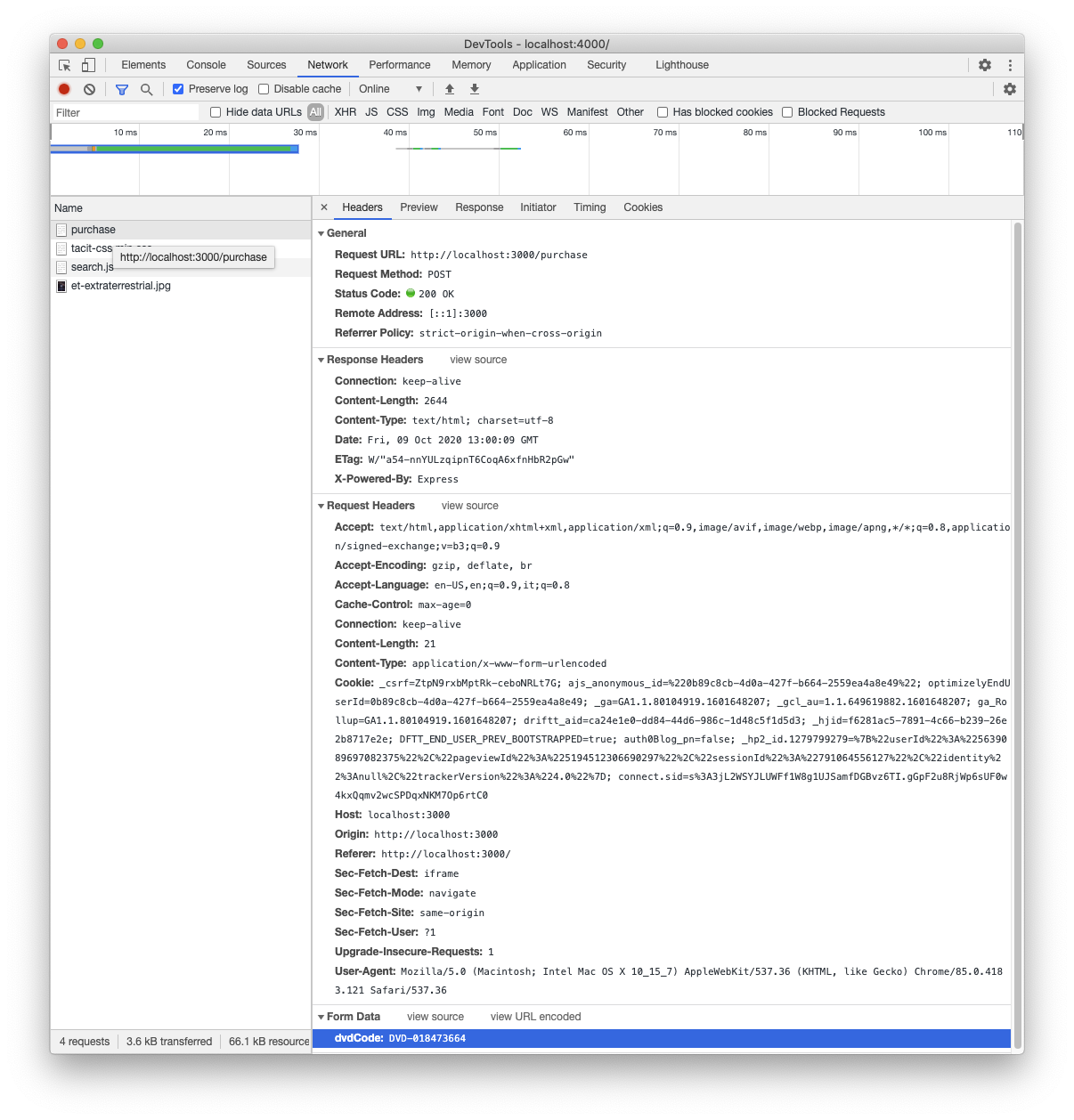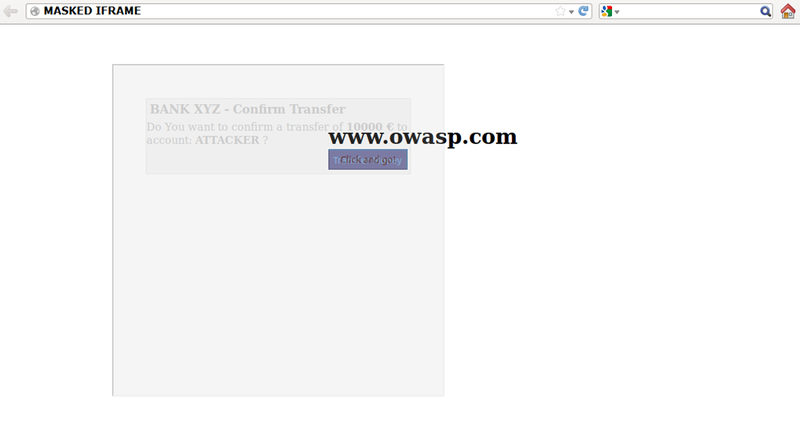
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo

ClickJacking Vulnerability | Click-Sec Tool | Indian Cyber Troops | Bug Bounty | Bug Hunting | ICT - YouTube
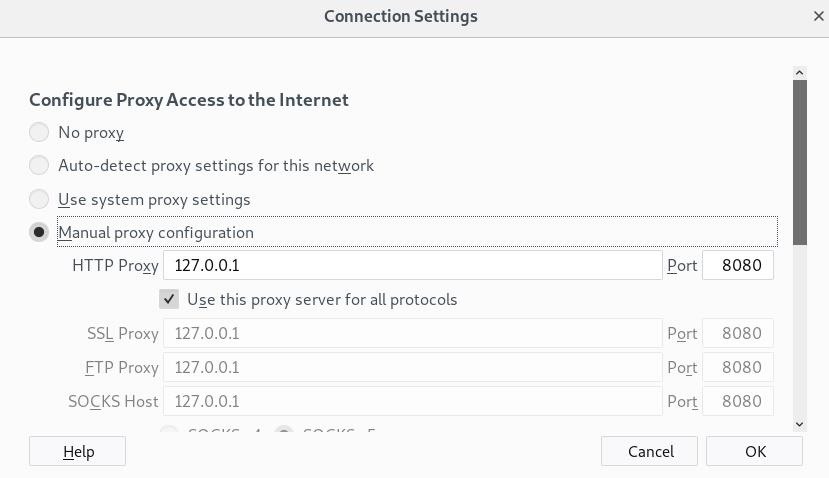
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo
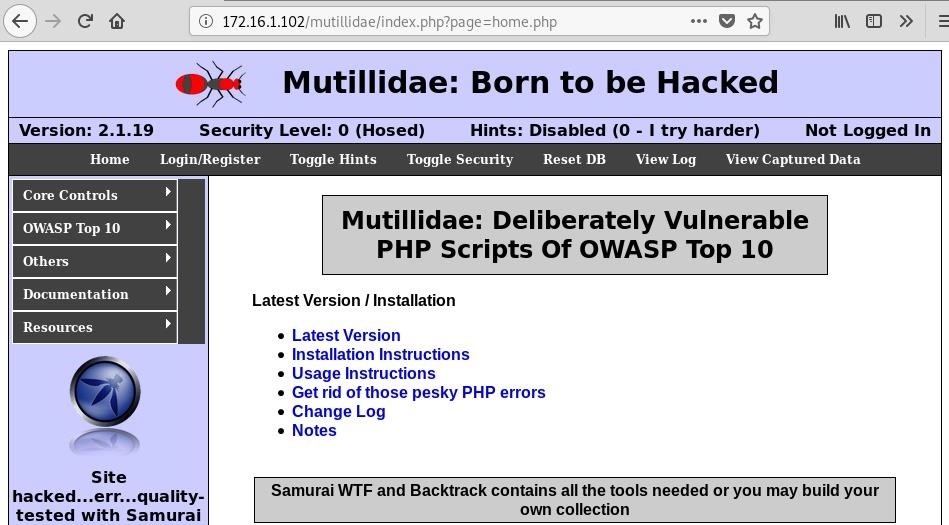
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo

How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo
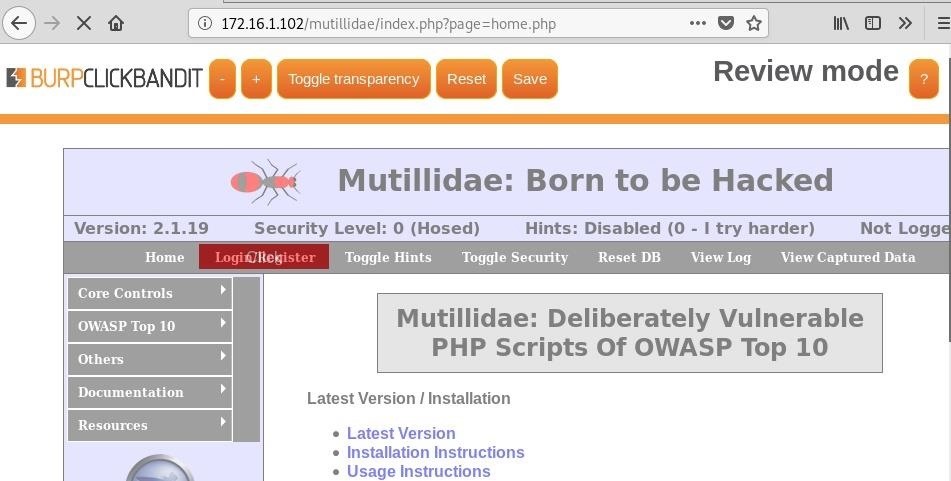
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo
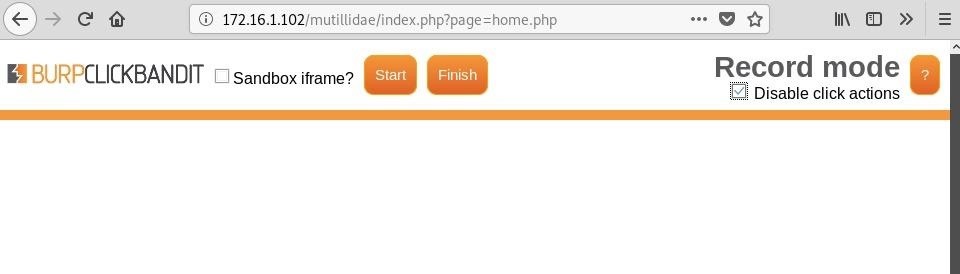
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo