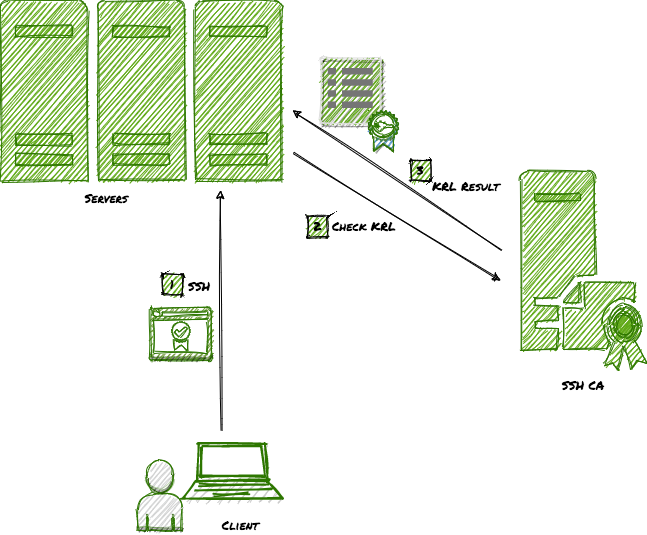
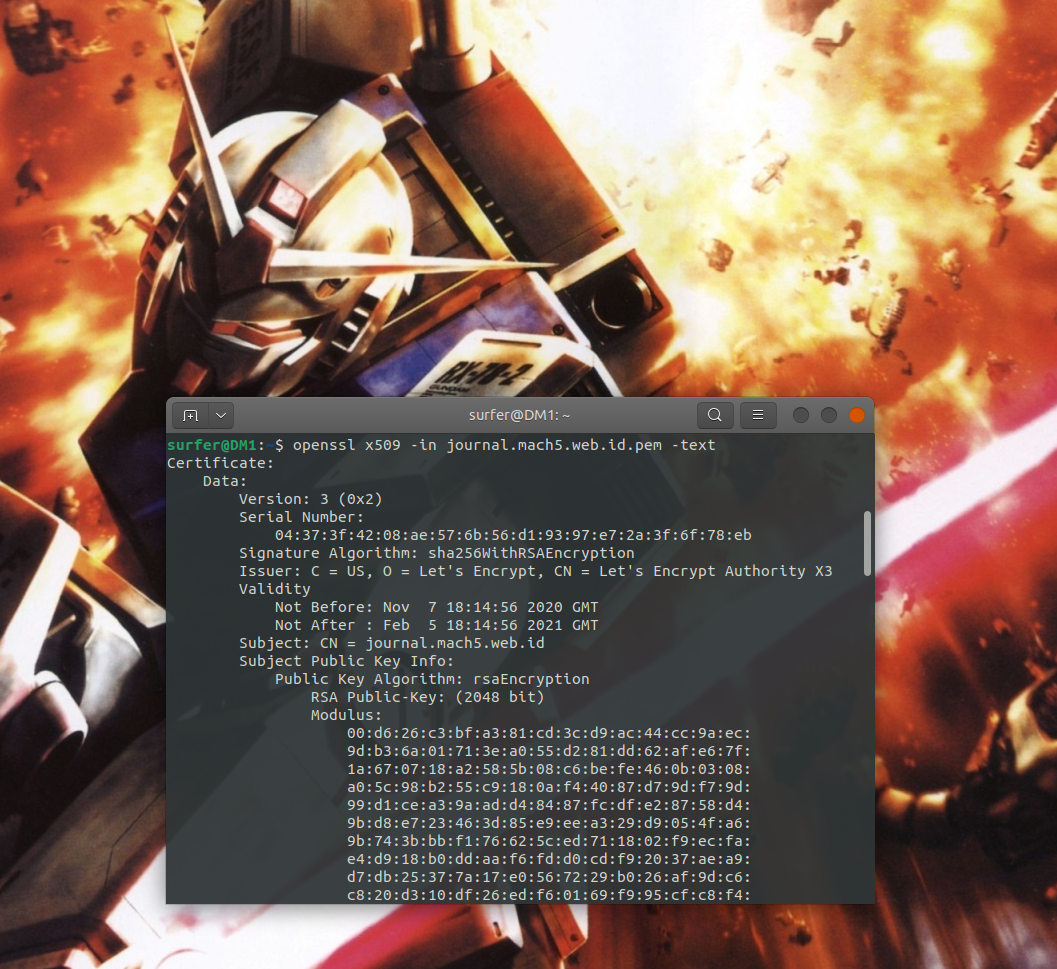
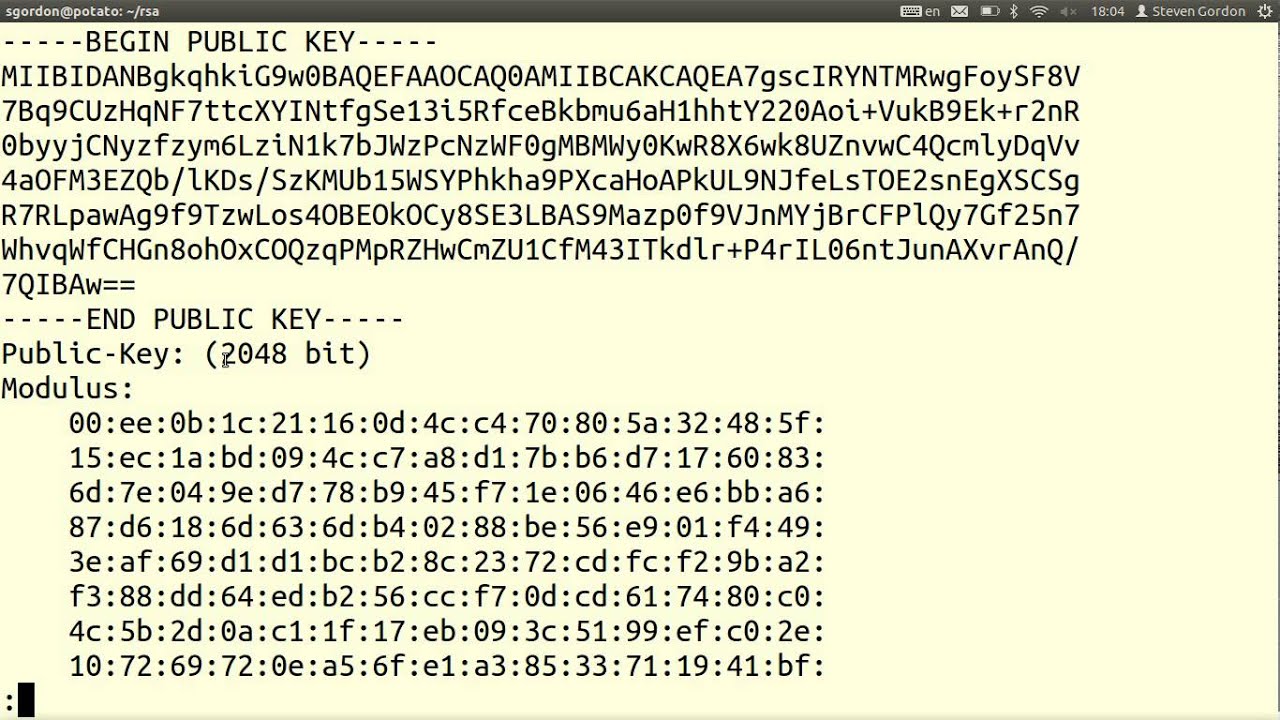
SHA-512 checksum summary Service and recovery pack FB14 Service pack.zip: de d8 12 31 cf 1f 0d c2 4f 4b 1e 8e c3 1a 43 47 52 a0

Threat Analysis: Active C2 Discovery Using Protocol Emulation Part2 (Winnti 4.0) - VMware Security Blog - VMware